Blogs

Recently, we came across a business requirement where we had to save API keys (secured date) in OSGI service. One of the recommendations based on Adobe Health Check is to encrypt data (API keys) to store them in JCR more securely. The same can be achieved using Crypto Support in AEM.
The Crypto Support Bundle provides a service which encrypts/decrypts binary or String data in AEM. On exploring further, it seems to be nailing the issue of encryption and decryption in just a few minutes. Crypto support is necessary to store the password in a salted or hashed form in the JCR so as to make the password storage secure and to avoid any breach.
The following steps will elaborate the mechanism to generate an encrypted key.
Step 1: Protecting the Plain Text
Crypto Support bundle provides a service that allows users to generate the “Protected Text” from the “Plain Text” input.
Open the URL http://<host>:<port>/<system/console/crypto>
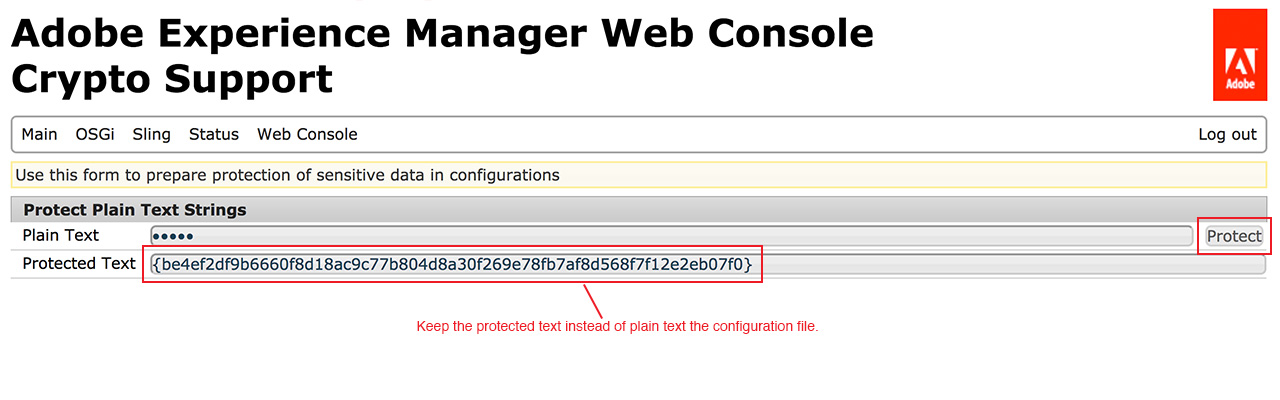
In the “Plain Text” field, add the string which needs to be encrypted and press the protect button. “Protected Text” field will show the encrypted string to be used. plain text string The encryption algorithm used in this procedure is symmetric key encryption namely AES algorithm, CBC mode with PKCS5 padding used from RSA JSafe library.
For instance, while setting up the SMTP configurations, it is not ideal to keep the password as a plain text in the OSGI config. Best way to do is to encrypt the password using Crypto Support and then use the Protected Text in the SMTP Configurations.
Next step is to decrypt the protected text in the backend code so as to fetch the original password, which is easy.
Step 2: Decrypt the Protected Text.
Since the OSGI configuration has the “Protected Text” configured, it is required to decrypt the value before actually using it.
Following code sample is used to decrypt the password:
@Reference
private CryptoSupport cryptoSupport;
private void setEmailConfiguration(Object smtpHost,Object smtpPort,Object smtpUser,Object smtpPwd,Object from Address){
String password=PropertiesUtil.toString(smtpPwd,StringUtil.EMPTY);
if(this.cryptoSupport.isProtected(password)){
this.smtpPassword=this.cryptoSuport.unProtect(password);
} else {
this.smtpPassword=password;
}
}The method unprotect(String cipherText) unprotects (decrypts) the string to return the plain text. We can also check if the String is already protected by using isProtected(String text)method. This method returns true if String provided is protected.
Note that we are not done yet. The protected string generated by Crypto Support will be different for different instances. One last step is required to make sure same protected text can be used throughout. It is an optional step, if different protected strings need to be used on different instances.
Step 3 (Optional): To Make the Protected Text Same for all the AEM Instances.
If we intend to use the same protected text for all the environments (it is recommended to use different password for production environment to ensure data integrity), then we need to follow below steps.
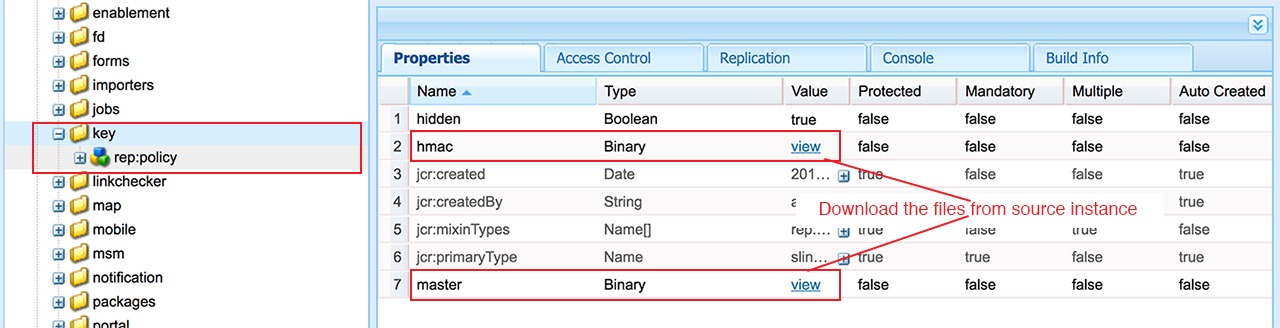
- Download the hmac and master files from the /etc/key current instance. The encryption uses a key which is created with AEM installation in OS filesystem under crx-quickstart. These are binary files which are randomly generated at start of Adobe Granite Crypto Support bundle.

- Create the /etc/key node for the destination instance and copy the above two files.
- Deploy the code and make sure to restart “com.adobe.granite.crypto” for very first time you upload these key and make cryptography effective.
Note: If we manually stop the Crypto Support bundle, then AEM login fails and the user will be unable to login with any user. Hence, it is always recommended to use CURL command at root directory of the server with admin user only to restart the crypto support bundle.
CURL command to stop the bundle:
curl -u admin:admin
http://<host>:<port>/system/console/bundles/com.adobe.granite.crypto -F action=stop
CURL command to start the bundle:
curl -u admin:admin
http://<host>:<port>/system/console/bundles/com.adobe.granite.crypto -F action=start
Hope this helps you all to smoothly implement encryption/decryption of the passwords!
We have tested this on AEM 6.2










Nice
Hello, I mistakenly stopped the bundle manually and I am unable to login now. Can you please help me resolve this issue.
AEM login depends on the same crypto bundle and hence you are unable to login when Crypto Bundle is stopped. In this case, AEM instance has to be restarted in order to refresh the state to original.
You can also start the bundle via CURL command, if you know the ID of crypto bundle.
Please note that since AEM 6.3, the crypto keys are no longer stored in JCR, but instead on the local HDD in the “Adobe Granite Crypto Bundle Key Provider” bundle folder:
– crx-quickstart/launchpad/felix/bundle[number]/data
Very interesting blog post. Quite informative and very helpful. This indeed is one of the recommended blogs for learners. Thank you for providing such a nice piece of article. I’m glad to leave a comment. Expect more articles in the future.