Blogs
Q1. What is clickjacking?
Clickjacking, also known as a “UI redress attack”, is when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link to another page when they were intending to click on the top level page. Thus, the attacker is “hijacking” clicks meant for their page and routing them to another page, most likely owned by another application, domain, or both.
If you’re still not clear about this concept then watch the video below.
Q2. How to stop clickjacking in AEM through the Apache2 Server?
Q3. What is the syntax of this configuration?
Header set X-Frame-Options: “sameorigin”
Q4. Where do we find the X-Frame-Options configuration?
- Uncomment this setting and restart your Apache2 server.
- Copy and paste this setting in apache2.conf file, uncomment it, and restart your Apache server.
While learning how to secure apache from clickjacking, I copied and pasted this setting in apache2.conf file, uncommented it and restarted my Apache2 server.
Q5. Apache Server is throwing error when restarting after this configuration?
Q6. How to enable Headers.mod in Apache2 server?
For enabling this module you have a headers.load file present in mods-available directory in your Apache2 server. In my case, it is present at /etc/apche2/mods-available. Just do one thing, create a softlink in your mods-enabled folder. If you are an Ubuntu user execute this command-
ln -s /etc/apache2/mods-available/header.load /etc/apache2/mods-enabled/headers.load
Q7. How to check whether the configuration is working or not?
After restarting the Apache2 server, just hit a non-cached page via Apache2 Server. Open debugger and check the response header. You will see X-Frame-Options header field as shown below.
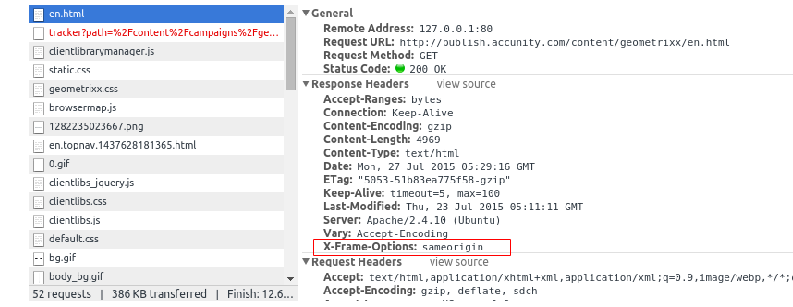
If you get this option on your page it means your configuration is working well and you’ve learnt how to secure apache from clickjacking.
Read about other solutions for problems in AEM working in our blog. Argil DX comes up with innovative ideas, tools and solutions to help developers and businesses get the best out of their Experience Manager implementation.